Istio Mixer Adapters.
Quick article about Mixer and adapters , one of the things i wanted to find out is what’s the involvement of Istio/Mixer when traffic is sent from one pod to another , having that kind of segregation or isolation could be useful , for example let’s imagine a 3 tier app in 3 different pods , you wouldn’t want your view layer speaking directly with the model , for example:
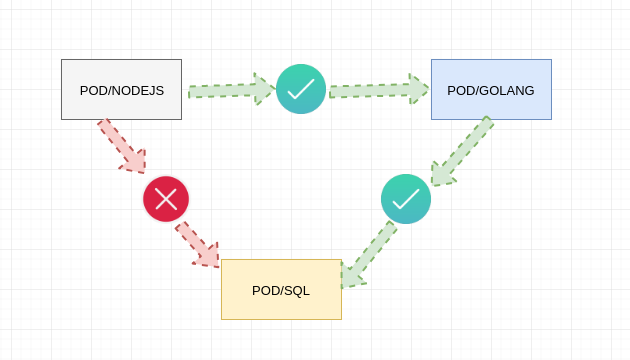
The goal is very clear , traffic between POD/NODE and POD/GOLANG should flow fine , but when POD/NODE want’s to tapo into POD/SQL that should not be allowed , this could be for a number or reasons .
I could think of a number of ways to do this alone in istio , maybe a hiden header or cookie between the sql (sidecar on to) and golang. (imagine that golang has to pass a jwt or a cookie to validate requests).Maybe also a different MTLS configuration signed by a different CA.
You could also do a simple rule like:
If i pass the header
secret=sauce
I’ll get through to the service
nginx
so let’s see how would that work (from a pod istio injected to nginx(which is also istio injected))
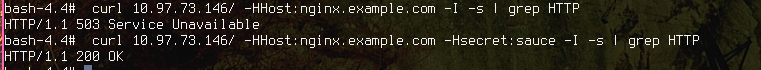
So i get a 200 when i pass the
secret
header wit the
sauce
value.
It’s also interesting to note that when you troubleshooting all these things mixer has a lot of really interesting info (there’s a number of ways to check this but for now let’s do kubectl logs)
k logs yourtelemetrypod -n istio-system -f
So for the failed request we get:
{“level”:”info”,”time”:”2018–07–24T09:34:47.539084Z”,”instance”:”accesslog.logentry.istio-system”,”apiClaims”:””,”apiKey”:””,”apiName”:””,”apiVersion”:””,”connectionMtls”:false,”destinationIp”:”172.17.0.16",”destinationNamespace”:”istio-system”,”destinationService”:”istio-policy.istio-system.svc.cluster.local”,”latency”:”1.020214ms”,”method”:”POST”,”originIp”:”0.0.0.0",”protocol”:”http”,”receivedBytes”:1157,”referer”:””,”requestOperation”:””,”requestSize”:800,”responseCode”:200,”responseSize”:51,”responseTimestamp”:”2018–07–24T09:34:47.540108Z”,”sentBytes”:219,”sourceIp”:”172.17.0.13",”sourceNamespace”:”istio-system”,”sourceService”:”istio-ingressgateway.istio-system.svc.cluster.local”,”sourceUser”:””,”url”:”/istio.mixer.v1.Mixer/Check”,”userAgent”:””}
{“level”:”info”,”time”:”2018–07–24T09:34:47.541322Z”,”instance”:”accesslog.logentry.istio-system”,”apiClaims”:””,”apiKey”:””,”apiName”:””,”apiVersion”:””,”connectionMtls”:false,”destinationIp”:”172.17.0.16",”destinationNamespace”:”istio-system”,”destinationService”:”istio-policy.istio-system.svc.cluster.local”,”latency”:”1.224358ms”,”method”:”POST”,”originIp”:”0.0.0.0",”protocol”:”http”,”receivedBytes”:981,”referer”:””,”requestOperation”:””,”requestSize”:624,”responseCode”:200,”responseSize”:51,”responseTimestamp”:”2018–07–24T09:34:47.542495Z”,”sentBytes”:219,”sourceIp”:”172.17.0.19",”sourceNamespace”:”default”,”sourceService”:”nets.default.svc.cluster.local”,”sourceUser”:””,”url”:”/istio.mixer.v1.Mixer/Check”,”userAgent”:””}
{“level”:”info”,”time”:”2018–07–24T09:34:47.540899Z”,”instance”:”accesslog.logentry.istio-system”,”apiClaims”:””,”apiKey”:””,”apiName”:””,”apiVersion”:””,”connectionMtls”:false,”destinationIp”:”172.17.0.19",”destinationNamespace”:”default”,”destinationService”:”nets.default.svc.cluster.local”,”latency”:”2.389636ms”,”method”:”HEAD”,”originIp”:”0.0.0.0",”protocol”:”http”,”receivedBytes”:872,”referer”:””,”requestOperation”:””,”requestSize”:0,”responseCode”:503,”responseSize”:57,”responseTimestamp”:”2018–07–24T09:34:47.543193Z”,”sentBytes”:149,”sourceIp”:”172.17.0.13",”sourceNamespace”:”default”,”sourceService”:”nets.default.svc.cluster.local”,”sourceUser”:”kubernetes://nets-57cdb6d9d7-rj7jk.default”,”url”:”/”,”userAgent”:”curl/7.60.0"}
{“level”:”info”,”time”:”2018–07–24T09:34:47.538628Z”,”instance”:”accesslog.logentry.istio-system”,”apiClaims”:””,”apiKey”:””,”apiName”:””,”apiVersion”:””,”connectionMtls”:false,”destinationIp”:”172.17.0.13",”destinationNamespace”:”istio-system”,”destinationService”:”istio-ingressgateway.istio-system.svc.cluster.local”,”latency”:”5.990164ms”,”method”:”HEAD”,”originIp”:”0.0.0.0",”protocol”:”http”,”receivedBytes”:628,”referer”:””,”requestOperation”:””,”requestSize”:0,”responseCode”:503,”responseSize”:0,”responseTimestamp”:”2018–07–24T09:34:47.544296Z”,”sentBytes”:122,”sourceIp”:”172.17.0.19",”sourceNamespace”:”default”,”sourceService”:”nets.default.svc.cluster.local”,”sourceUser”:”kubernetes://nets-57cdb6d9d7-rj7jk.default”,”url”:”/”,”userAgent”:”curl/7.60.0"}
{“level”:”info”,”time”:”2018–07–24T09:34:48.541291Z”,”instance”:”accesslog.logentry.istio-system”,”apiClaims”:””,”apiKey”:””,”apiName”:””,”apiVersion”:””,”connectionMtls”:false,”destinationIp”:”172.17.0.14",”destinationNamespace”:”istio-system”,”destinationService”:”istio-telemetry.istio-system.svc.cluster.local”,”latency”:”8.229042ms”,”method”:”POST”,”originIp”:”0.0.0.0",”protocol”:”http”,”receivedBytes”:1305,”referer”:””,”requestOperation”:””,”requestSize”:980,”responseCode”:200,”responseSize”:5,”responseTimestamp”:”2018–07–24T09:34:48.549353Z”,”sentBytes”:174,”sourceIp”:”172.17.0.16",”sourceNamespace”:”istio-system”,”sourceService”:”istio-mixer.istio-system.svc.cluster.local”,”sourceUser”:””,”url”:”/istio.mixer.v1.Mixer/Report”,”userAgent”:””}
{“level”:”info”,”time”:”2018–07–24T09:34:48.544250Z”,”instance”:”accesslog.logentry.istio-system”,”apiClaims”:””,”apiKey”:””,”apiName”:””,”apiVersion”:””,”connectionMtls”:false,”destinationIp”:”172.17.0.14",”destinationNamespace”:”istio-system”,”destinationService”:”istio-telemetry.istio-system.svc.cluster.local”,”latency”:”8.098142ms”,”method”:”POST”,”originIp”:”0.0.0.0",”protocol”:”http”,”receivedBytes”:1069,”referer”:””,”requestOperation”:””,”requestSize”:744,”responseCode”:200,”responseSize”:5,”responseTimestamp”:”2018–07–24T09:34:48.552195Z”,”sentBytes”:174,”sourceIp”:”172.17.0.19",”sourceNamespace”:”default”,”sourceService”:”nets.default.svc.cluster.local”,”sourceUser”:””,”url”:”/istio.mixer.v1.Mixer/Report”,”userAgent”:””}
{“level”:”info”,”time”:”2018–07–24T09:34:48.552645Z”,”instance”:”accesslog.logentry.istio-system”,”apiClaims”:””,”apiKey”:””,”apiName”:””,”apiVersion”:””,”connectionMtls”:false,”destinationIp”:”172.17.0.14",”destinationNamespace”:”istio-system”,”destinationService”:”istio-telemetry.istio-system.svc.cluster.local”,”latency”:”4.24435ms”,”method”:”POST”,”originIp”:”0.0.0.0",”protocol”:”http”,”receivedBytes”:1237,”referer”:””,”requestOperation”:””,”requestSize”:912,”responseCode”:200,”responseSize”:5,”responseTimestamp”:”2018–07–24T09:34:48.556842Z”,”sentBytes”:174,”sourceIp”:”172.17.0.13",”sourceNamespace”:”istio-system”,”sourceService”:”istio-ingressgateway.istio-system.svc.cluster.local”,”sourceUser”:””,”url”:”/istio.mixer.v1.Mixer/Report”,”userAgent”:””}
And for the one that worked:
{"level":"info","time":"2018-07-24T09:34:54.741027Z","instance":"accesslog.logentry.istio-system","apiClaims":"","apiKey":"","apiName":"","apiVersion":"","connectionMtls":false,"destinationIp":"172.17.0.4","destinationNamespace":"default","destinationService":"nginx.default.svc.cluster.local","latency":"2.51907ms","method":"HEAD","originIp":"0.0.0.0","protocol":"http","receivedBytes":883,"referer":"","requestOperation":"","requestSize":0,"responseCode":200,"responseSize":0,"responseTimestamp":"2018-07-24T09:34:54.743548Z","sentBytes":200,"sourceIp":"172.17.0.13","sourceNamespace":"default","sourceService":"nets.default.svc.cluster.local","sourceUser":"kubernetes://nets-57cdb6d9d7-rj7jk.default","url":"/","userAgent":"curl/7.60.0"}
{"level":"info","time":"2018-07-24T09:34:54.740708Z","instance":"accesslog.logentry.istio-system","apiClaims":"","apiKey":"","apiName":"","apiVersion":"","connectionMtls":false,"destinationIp":"172.17.0.13","destinationNamespace":"istio-system","destinationService":"istio-ingressgateway.istio-system.svc.cluster.local","latency":"3.603382ms","method":"HEAD","originIp":"0.0.0.0","protocol":"http","receivedBytes":639,"referer":"","requestOperation":"","requestSize":0,"responseCode":200,"responseSize":0,"responseTimestamp":"2018-07-24T09:34:54.744135Z","sentBytes":200,"sourceIp":"172.17.0.19","sourceNamespace":"default","sourceService":"nets.default.svc.cluster.local","sourceUser":"kubernetes://nets-57cdb6d9d7-rj7jk.default","url":"/","userAgent":"curl/7.60.0"}
{"level":"info","time":"2018-07-24T09:34:54.741426Z","instance":"accesslog.logentry.istio-system","apiClaims":"","apiKey":"","apiName":"","apiVersion":"","connectionMtls":false,"destinationIp":"172.17.0.16","destinationNamespace":"istio-system","destinationService":"istio-policy.istio-system.svc.cluster.local","latency":"1.185697ms","method":"POST","originIp":"0.0.0.0","protocol":"http","receivedBytes":1066,"referer":"","requestOperation":"","requestSize":710,"responseCode":200,"responseSize":51,"responseTimestamp":"2018-07-24T09:34:54.742529Z","sentBytes":219,"sourceIp":"172.17.0.4","sourceNamespace":"default","sourceService":"nginx.default.svc.cluster.local","sourceUser":"","url":"/istio.mixer.v1.Mixer/Check","userAgent":""}
{"level":"info","time":"2018-07-24T09:34:55.743929Z","instance":"accesslog.logentry.istio-system","apiClaims":"","apiKey":"","apiName":"","apiVersion":"","connectionMtls":false,"destinationIp":"172.17.0.14","destinationNamespace":"istio-system","destinationService":"istio-telemetry.istio-system.svc.cluster.local","latency":"3.483434ms","method":"POST","originIp":"0.0.0.0","protocol":"http","receivedBytes":1236,"referer":"","requestOperation":"","requestSize":912,"responseCode":200,"responseSize":5,"responseTimestamp":"2018-07-24T09:34:55.747342Z","sentBytes":174,"sourceIp":"172.17.0.4","sourceNamespace":"default","sourceService":"nginx.default.svc.cluster.local","sourceUser":"","url":"/istio.mixer.v1.Mixer/Report","userAgent":""}
{"level":"info","time":"2018-07-24T09:34:55.744173Z","instance":"accesslog.logentry.istio-system","apiClaims":"","apiKey":"","apiName":"","apiVersion":"","connectionMtls":false,"destinationIp":"172.17.0.14","destinationNamespace":"istio-system","destinationService":"istio-telemetry.istio-system.svc.cluster.local","latency":"2.92787ms","method":"POST","originIp":"0.0.0.0","protocol":"http","receivedBytes":1333,"referer":"","requestOperation":"","requestSize":1008,"responseCode":200,"responseSize":5,"responseTimestamp":"2018-07-24T09:34:55.747057Z","sentBytes":174,"sourceIp":"172.17.0.13","sourceNamespace":"istio-system","sourceService":"istio-ingressgateway.istio-system.svc.cluster.local","sourceUser":"","url":"/istio.mixer.v1.Mixer/Report","userAgent":""}
{"level":"info","time":"2018-07-24T09:34:55.743733Z","instance":"accesslog.logentry.istio-system","apiClaims":"","apiKey":"","apiName":"","apiVersion":"","connectionMtls":false,"destinationIp":"172.17.0.14","destinationNamespace":"istio-system","destinationService":"istio-telemetry.istio-system.svc.cluster.local","latency":"3.811374ms","method":"POST","originIp":"0.0.0.0","protocol":"http","receivedBytes":1044,"referer":"","requestOperation":"","requestSize":719,"responseCode":200,"responseSize":5,"responseTimestamp":"2018-07-24T09:34:55.747434Z","sentBytes":174,"sourceIp":"172.17.0.16","sourceNamespace":"istio-system","sourceService":"istio-mixer.istio-system.svc.cluster.local","sourceUser":"","url":"/istio.mixer.v1.Mixer/Report","userAgent":""}
So that gives you a clue of how heavy is the involvement of mixer on the whole flow , there’s a lot of caching on envoy so each requests doesn’t tap on mixer but enough traffic flows between the two.
Mixer Adapters:
Another way of doing this would be with a mixer adapter (denier for example) , where you could deny access from a given pod altogether.
For example look at this denier+rule combo:
It’s pretty self explanatory (but if you wanna read more , you can look at https://istio.io/docs/tasks/security/secure-access-control/)
So basically it’s a denier handler that reacts on the rule that if the request tries to land on app==nginx from a source namespace== default , it should get some kind of error (403) likely:
And this is the result:

pretty neat , the cool thing about this is you can do all sorts of combinations , for example we could block based on useragent , or service account , etc.
There’s a few adapters available for mixer but writing your own isn’t that complicated , you can easily integrate with other services and endpoints .
I hope this gives you an idea of how flexible this whole thing is , it’s really up to you to implement it in whatever way you find more comfortable.