Leaked “malware” OutlawCountry review
This week there was a reported leak coming “supposedly” from some security agency , It’s called OC (OutLawCountry) , and i don’t know if it should be called malware because it really doesn’t need to exploit anything to be fair .
OC , It’s supposed to route some or all your traffic to a specific endpoint , but the catch is that this “malware” comes prepackaged in a kernel object (.ko) , a kernel module!!
 oc kernel module
oc kernel module
This is a bit mind boggling , so they can certainly do everything you would wanna do from a kernel module , routes, iptables rules , etc etc … But why a kernel module ?
Well i feel it’s a neat way to prepackage and drop it but also i feel that it woud be something that might failt depending on the kernel version and compilation flags etc.
So I’ve decided to “re-create” what the “malware” might be doing.
OC details:
As we’ve mentioned this comes a kernel module and in theory it creates a new iptables “table”. Now this isn’t a new chain or a new rule or anything similar , this is a new “table” such as filter,nat or mangle:

That’s the name of the table “dpxvke8h18” , so to see the rules you would need to do something like:
iptables -nvL -t dpxvke8h18 // iptables -S -t dpxvke8h18
So part of me is thinking by putting it in a different table it’s kind of “harder” for an admin to know that the table exists and might not look up the rules attached to the table.
Tables:
Kernel iptables tables are created at compile time and normall come as modules, if we pick “mangle” for example:
The file iptable_mangle.c , it’s a kernel module itself:
module_init(iptable_mangle_init);
module_exit(iptable_mangle_fini);
Moduled have an init and an exit function , these two are called on insmod/modprobe and rmmod for exmaple.
iptable_mangle is loaded in most system so if you do:
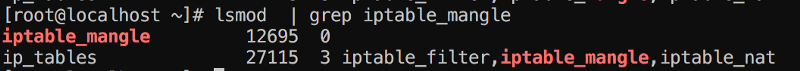
Creating a new table:
So I don’t really know if there’s a way to do this from userland , but in an intent to replicate what OC is doing I’ve literally copied most of the data from iptable_mangle and change a few names:
nf_foobar.c
So the code is kind of self explanatory , even if you don’t have a clue about kernel development , here’s the most important functions:
repl = ipt_alloc_initial_table(&packet_mangler); ret = ipt_register_table(net, &packet_mangler, repl);
We alloc the table and then register , remember struct net is the “network namespace/stack” we’re we attaching this rule (init_net).
You can go ahead and extend this and add rules to it etc , but i won’t do it in this article.
Compiling nf_foobar:
I’m gisting a makefile , that allow to compile into a .o and .ko , of course when they’re dropping this into powned servers they’re not compiling them in place the probably just drop the .ko and load it as you load drivers for your winmodem :)
Loading and testing it:
So this is what happens without the mod:
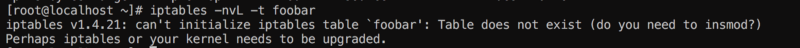
Makes perfect sense , it also suggests that tables are .ko , let’s compile and insmod:
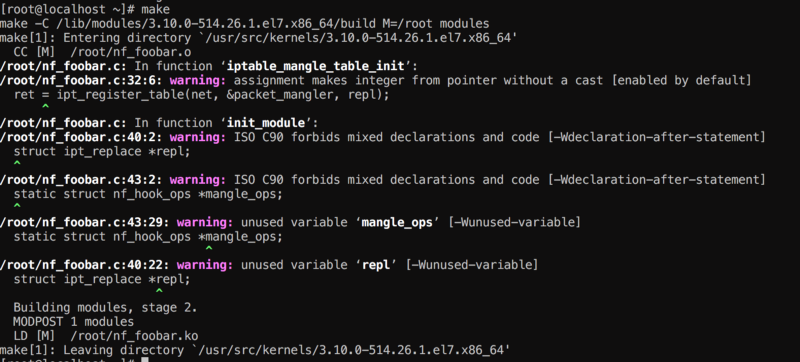 compiling my specific table
compiling my specific table
Some warnings , are expected :)
insmod nf_foobar.ko
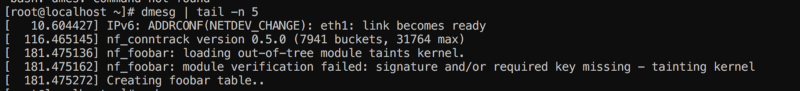
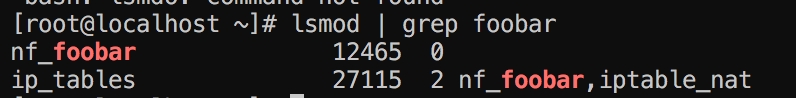
Alright so good stuff now we need to see with iptables if the table exists:
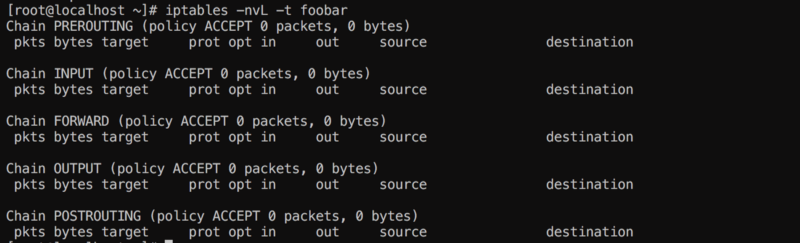 foobar table
foobar table
Nice , so now we have a new iptables “table” where you can add rules , just like nat,mangle or filter.
Now when you remove the module you can avoid unregistering the table so the table remains there after the module is unloaded ;)
Last Notes:
So that’s it , i guess questions for my humble 200 followers is why do you think they’ve decided to use this transport (.ko) and not nft , or not adding rules to the table mangle or soemthing like that , I will think about it too.
Thank you!