Vault as CA with PKI backend
I’m gonna show how to run your own CA within pki framework , and be able to generate private keys and sign certificates. We will do this with vault , just because it’s the fastest way to get it done.
Download and run Vault:
Make sure you get it from https://www.vaultproject.io/downloads.html or you build it by hand whatever you prefer.
We will run this in development mode for this tutorial but make sure you do something better if you’re running this in production.
vault server -dev
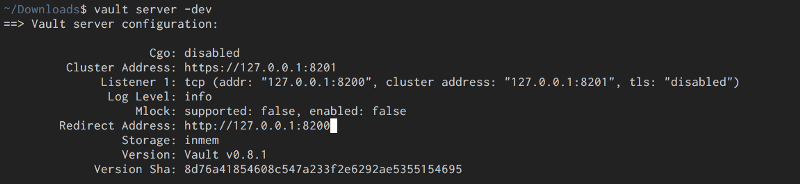
That simple , one thing to notice is that you will need to export and env variable to let vault know which vault server to use:
export VAULT_ADDR='[http://127.0.0.1:8200'](http://127.0.0.1:8200%27)
Creating the PKI backend
Vault has plug-able backends , so we need to mount the backend we want to use , for that reason:
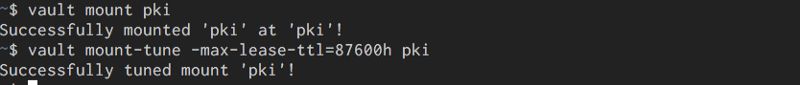
vault mount pki
vault mount-tune -max-lease-ttl=87600h pki
Generate the Root certificate
We will issue certs directly from the root , not using intermediates , so let’s create the root cert that the CA will use:
vault write pki/root/generate/internal common_name=internal.com ttl=87600h
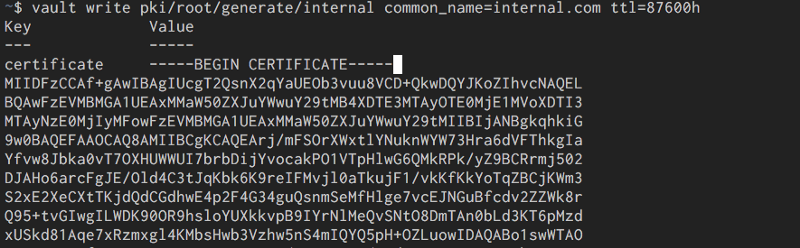
Keys and certs will be store in the backend
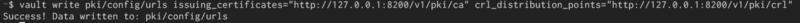
Configure CRLs for the CA:
vault write pki/config/urls issuing_certificates="[http://127.0.0.1:8200/v1/pki/ca](http://127.0.0.1:8200/v1/pki/ca)" crl_distribution_points="[http://127.0.0.1:8200/v1/pki/crl](http://127.0.0.1:8200/v1/pki/crl)"
Creating a Role
We gonna create a role like a policy that allows us to generate certs/keys or credentials :
vault write pki/roles/jerrycom allowed_domains="jerry.com" allow_subdomains="true" max_ttl="72h"
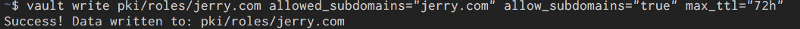
So the policy allows me to generate credentials for the domain jerry.com and it allows the creation of subdomains.
Issuing a crt and a private key
Finally we get to create the credentials that we will need to use in different services over tls
vault write pki/issue/jerrycom common_name=blah.jerry.com
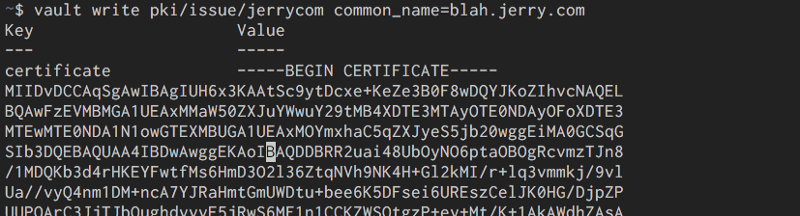
From the command above you will get a key and a crt ,
-----BEGIN CERTIFICATE-----
and
-----BEGIN RSA PRIVATE KEY-----
If you want to verify if these match , as the crt has been signed with the priv key , save the crt in a file and the key in a different file and run:
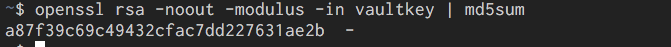
For the key:
openssl rsa -noout -modulus -in vaultkey | md5sum
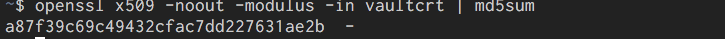
For the CRT:
openssl x509 -noout -modulus -in vaultcrt | md5sum
You could also load them into nginx and test them with a browser for example .
Thank you.
